Authentication
Initial Concepts
Even though you might not have heard the name, you’ve definitely used authentication in your life. Authentication is the method by which a person or system proves that they are who they say they are. In fact, since not just people can undergo authentication, the entities (people, computers, devices, etc.) being authenticated are instead referred to as subjects.
Some important definitions are:
- Identification - the act of a subject claiming an identity with some identifier such as a username or email address
- Authentication - the act of proving that a given subject is the identity they are claiming to be
- Authorization - the act of granting resource access and permission based on the authenticated identity
- Accounting - the act of tracking user activity and recording the activity in logs
The last three actions: authentication, authorization, and accounting are typically referred to as AAA. Do also note that there’s an important distinction between identification and authentication. Identification is typically based on an easily known identity like a username or email and is usually publicly known or at least easy to know. Authentication on the other is used to prove an identity and should always be based on private factors such as a password.
In addition, with authentication only two entities should have knowledge of the credentials, the user and the entity performing the authentication. However, this does not mean the entity performing the authentication has to know the exact authentication factor (more on these later). The authenticator just has to know enough about the factor to reliably prove a given identity.
Authentication Factors
Authentication is performed using some set of factors. An authentication setup may use one or more of these factors depending on how secure the authentication needs to be. These factors are:
- Something you know, like a password or personal identification number (PIN)
- Something you have, like a smart card or USB token
- Something you are, like a fingerprint
Something You Know
The something you know authentication factor refers to a shared secret like a password or PIN. Security questions also fall under this factor, however, due to the fact that they’re typically easy to search and find online, it’s not recommended to use security questions as your primary or only authentication method.
This authentication factor is also the least secure form of authentication. This is typically due to password and PIN misuse. In fact, 123456 and password have been the top two most used passwords for the past five years according to splashdata.
Now in an ideal world users should be well-informed about good password behaviors, but as they typically aren’t this tends to lead to poor passwords, password reuse, poor password storage and so on that makes it easier to be stolen. For those interested in knowing more about proper password use/behavior, read-on, otherwise skip down to the something you have section. Good passwords and proper password behaviors follow the following practices:
- Have characters that aren’t just a-z: This means using numbers, capital letters, special characters ($, @, etc.) and maybe even symbols and letters from languages you don’t natively speak. While this change doesn’t seem to matter much, consider that it takes just 100 hours to test all 6-letter combinations using letters of only one case. However, to test all 6-letter combinations using upper and lower case letters as well as numbers (not even counting special and other characters) takes 2 years.
- Are long: Longer is better when it comes to password safety. It’s much easier to generate all combinations of a password that’s max length is 5 versus a password with 12 or more characters. In fact, Microsoft recommends that a password should at least be 14 characters long.
- Aren’t located in a dictionary: This means avoiding using words that can be found in the dictionary. Note that instead of using something like dictionary, D!cti0n@ry is a valid alternative. Although, please don’t use just that as your password.
- Is easy to remember: It’s going to be a lot harder to remember a password that’s just a jumble of characters and as a result people typically write it down on a piece of paper. At that point, the password is no longer secure. Instead, it’s better to come up with a system to generate a password that you can easily remember. However, make sure the system isn’t too obvious or easy to guess. Many password cracking tools know to swap 0 or o, 1 for l and so on.
- Is not reused: It’s a bad idea to reuse the same password across accounts as once an attacker has broken one account, they now have access to the rest of your accounts.
- Is changed frequently: Keeping the same password for an account forever makes it easier for that account to be compromised. If the system holding you account is ever attacked and the attacker gains access to stored password details, if you’re not changing your password, you’re at risk. In addition, if an attacker successfully determines your password they’re now able to login whenever they want. However, by changing your password frequently (usually ever 45 days) you shorten the window by which an attacker can guess a given password before having to try again.
- Is not written down: Having a piece of paper with your account details is almost the same as just telling people your account details, it’s better to not write it down at all.
Now with the wide number of accounts you typically need, ensuring proper password behavior and remembering the passwords can be difficult. Due to this, password managers are starting to come into vogue. Password managers are software that help generate complex passwords as well as store them securely to be retrieved and used when needed. Accessing the password manager uses what is known as a master password, which unlocks access to the credentials stored within. This master password is also typically used to encrypt the credentials meaning even if the credentials are stolen they would need to be decrypted before using and could only be decrypted with the master password. Using a password manager can make proper password behavior easier as it can generate and store passwords as well as provide assistance in rotating them. There are various different options for password managers such as 1Password, Lastpass, and so on and I encourage you to look into which ones might seem appealing to you if you believe a password manager might be helpful for you.
Something You Have
The something you have authentication factor refers to an object in your possession. While this typically refers to something physical, that’s not always the case. As an example a smart card, a credit-card sized card that has an embedded microchip and certificate, or even a driver’s license are both an example of something that falls under the something you have factor.
In addition to cards and licenses, tokens an electronic device roughly the size of a car key or smaller can also be used. When needed for authentication, the user activates the token, typically by clicking a button on it, and it generates a series of digits or some other value that can then be entered into the authentication form. Tokens typically generate what is known as a one-time password which as the name suggests is a password that can only be used once before expiring. These one-time passwords are also usually time-based and will expire after a certain period of time, say 60 seconds, regardless of whether or not they have been used.
Something You Are
The something you are authentication factor uses biometrics, like fingerprints or iris scanning, to perform authentication. This method is typically considered the strongest form of authentication as it’s the most difficult to falsify. Some common biometrics used in authentication are:
- Fingerprints
- Retina and iris
- Voice
- Facial features
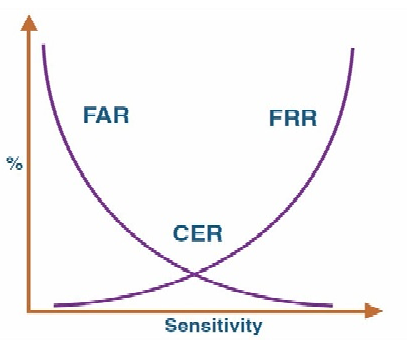
Biometric systems are not 100% accurate and allows you to adjust the sensitivity of the system. Due to this biometric systems might make a false reading. This could be a false positive or false acceptance where the biometric system incorrectly identifies an unauthorized user as an authorized user or a false negative or false rejection where the system incorrectly rejects an authorized user. As a biometric system becomes more sensitive, it typically increases the number of false rejections while decreasing the sensitivity increases the number of false positives. The crossover error rate for a biometric system is the level of sensitivity where the false acceptance rate crosses over with the false rejection rate, seen in the graph below. The lower the crossover error the more accurate a system.
Multifactor Authentication
Multifactor authentication is using two or more authentication factors together. Typically an authentication system that uses only two different authentication factors is called two-factor or dual-factor authentication. Note that these must be different authentication factors an authentication system that uses a password and a PIN is not considered multifactor. However, if it uses both a smart card and a password than it’s considered multifactor.